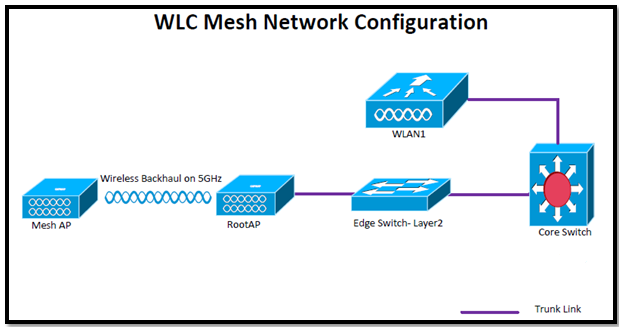
Nus Wireless Network Configuration Guide For Mac
This guide applies to user using Mac OS X 10.8 with 802.1x enabled network. Click on Network under Internet & Wireless system preference. Also, you should of course try connecting your Mac to another wireless network to see whether the problem persists. If you can connect to another WiFi setup, then consider noting down the router’s configuration and setup details and comparing that to your own. Learn network configuration guide with free interactive flashcards. Choose from 500 different sets of network configuration guide flashcards on Quizlet.
Know your wireless name (SSID) and password On a Plusnet router, the wireless name (SSID) will start with Plusnet and may have extra letters or numbers at the end, e.g. PlusnetWireless123456 or PlusnetABC123. Your wireless password (also known as the wireless key or WPA PSK) is 10 characters long. You'll find both printed on the bottom of your router and setup sticker (if included with your router). At the top right side of your screen and click the Wireless icon.


If Airport is switched off, select Turn Airport On (otherwise go to step 3). You'll see a list of networks you can connect to. Select your router's Wireless name (it'll start with PlusnetWireless).
You'll be asked for the password. This is the Wireless key (or WPA-PSK key) shown on the bottom of your router.
Enter the key and click OK. (If you're on MAC OS X 10.4 or below you'll also need to choose a Wireless Security type - select WPA Personal).
Having problems with this step?. Your wireless key is case sensitive, watch out for upper and lower case letters. Watch out for 0, that's a number zero rather than a letter O. You're now connected to your wireless network.
Open your web browser to start browsing! If you want to check your connection, the wireless icon at the top right side of your screen shows what's going on. The bars on the icon indicate the signal strength. Clicking the wireless icon will show the name of the network you're currently connected to.
Sntp server primary address 192.168.1.5 sntp enable radius server host 192.168.1.5 acct-enable radius server host key useStrongerSecret radius server host key useStrongerSecret used-by eapol radius server host key useStrongerSecret used-by non-eapol radius dynamic-server client 192.168.1.5 radius dynamic-server client 192.168.1.5 secret useStrongerSecret radius dynamic-server client 192.168.1.5 enable radius dynamic-server client 192.168.1.5 process-change-of-auth-requests radius dynamic-server client 192.168.1.5 process-disconnect-requests. Interface FastEthernet ALL vlan ports 1 tagging tagAll vlan members 2,3,4,5 1 vlan ports 1 pvid 2 eapol multihost port 1 enable eap-mac-max 8 allow-non-eap-enable non-eap-mac-max 8 radius-non-eap-enable use-radius-assigned-vlan non-eap-use-radius-assigned-vlan eap-packet-mode unicast adac-non-eap-enable eapol port 1 status auto traffic-control in re-authentication enable eapol port 1 radius-dynamic-server enable lldp port 1 vendor-specific avaya dot1q-framing tagged no adac detection port 1 mac adac port 1 tagged-frames-tagging tag-all adac port 1 enable spanning-tree port 1 learning fast. Class-map type control subscriber match-any INCRITICALAUTH match activated-service-template DEFAULTCRITICALVOICETEMPLATE match activated-service-template CRITICALAUTHVLAN match activated-service-template CRITICAL-ACCESS! Class-map type control subscriber match-none NOTINCRITICALAUTH match activated-service-template DEFAULTCRITICALVOICETEMPLATE match activated-service-template CRITICALAUTHVLAN match activated-service-template CRITICAL-ACCESS! Class-map type control subscriber match-all AAASVRDOWNUNAUTHDHOST match result-type aaa-timeout match authorization-status unauthorized! Class-map type control subscriber match-all AAASVRDOWNAUTHDHOST match result-type aaa-timeout match authorization-status authorized!
 Download drivers, software, firmware and manuals for your Canon product and get access to. Canon PIXMA MP280. PIXMA Software and App Descriptions. If you've got a Canon PIXMA MP280 and can't connect it to your Mac, this Canon PIXMA MP280 driver will fix it for you. It's specifically for the Canon PIXMA. The PIXMA MP280 Inkjet Photo All-In-One is a compact, stylish and high. With Microsoft Internet Explorer 7 in Windows 7, Windows Vista or Windows XP only. Download Canon PIXMA MP280 Driver for Mac now from Softonic: 100% safe and virus free. More than 99 downloads this month. Download Canon PIXMA. Setup Software & User's Guide CD-ROM MP280 Printer Driver Easy-PhotoPrint EX Easy Web-Print EX (Windows Only)4 Full HD Movie Print2 MP Navigator EX.
Download drivers, software, firmware and manuals for your Canon product and get access to. Canon PIXMA MP280. PIXMA Software and App Descriptions. If you've got a Canon PIXMA MP280 and can't connect it to your Mac, this Canon PIXMA MP280 driver will fix it for you. It's specifically for the Canon PIXMA. The PIXMA MP280 Inkjet Photo All-In-One is a compact, stylish and high. With Microsoft Internet Explorer 7 in Windows 7, Windows Vista or Windows XP only. Download Canon PIXMA MP280 Driver for Mac now from Softonic: 100% safe and virus free. More than 99 downloads this month. Download Canon PIXMA. Setup Software & User's Guide CD-ROM MP280 Printer Driver Easy-PhotoPrint EX Easy Web-Print EX (Windows Only)4 Full HD Movie Print2 MP Navigator EX.
Class-map type control subscriber match-all DOT1XNORESP match method dot1x match result-type method dot1x agent-not-found! Class-map type control subscriber match-all MABFAILED match method mab match result-type method mab authoritative! Class-map type control subscriber match-all DOT1XFAILED match method dot1x match result-type method dot1x authoritative.
Aaa group server radius packetfence server name packetfence! Aaa accounting update newinfo aaa accounting identity default start-stop group packetfence!! Device-sensor filter-list dhcp list dhcp-list option name host-name option name parameter-request-list option name class-identifier! Device-sensor filter-list lldp list lldp-list tlv name system-description! Device-sensor filter-list cdp list cdp-list tlv name version-type tlv name platform-type! Device-sensor filter-list dhcp list lldp-list device-sensor filter-spec dhcp include list dhcp-list device-sensor filter-spec lldp include list lldp-list device-sensor filter-spec cdp include list cdp-list device-sensor notify all-changes.
Nothing is required to activate VoIP on the switch, you must simply configure the voice VLAN you want PacketFence to assign in the PacketFence switch configuration as well as enabling VoIP there. Note that your phones must not tag their packets on the network and should send their traffic untagged when connected into a PacketFence enabled port. This means you should not have the voice VLAN capabilities enabled on the switch itself as they might conflict with the authorization attributes returned by PacketFence.
Snmp-server authentication-trap disable snmp-server host 192.168.1.5 'public' snmp trap link-status port 1-24 disable no mac-security mac-address-table interface FastEthernet ALL mac-security port ALL disable mac-security port 1-24 enable default mac-security auto-learning port ALL max-addrs exit mac-security enable mac-security snmp-lock disable mac-security intrusion-detect disable mac-security filtering enable mac-security snmp-trap enable mac-security auto-learning aging-time 60 mac-security learning-ports NONE mac-security learning disable VoIP support. Dot1x port-control mac-based dot1x re-authentication dot1x timeout reauth-period 1800 dot1x timeout supp-timeout 10 dot1x timeout guest-vlan-period 3 dot1x timeout server-timeout 1800 dot1x mac-auth-bypass dot1x unauthenticated-vlan 4 vlan participation include 1,2,3,4,5,100 voice vlan 100 auto-voip protocol-based lldp transmit lldp receive lldp transmit-tlv port-desc lldp transmit-tlv sys-name lldp transmit-tlv sys-desc lldp transmit-tlv sys-cap lldp transmit-mgmt lldp notification lldp med lldp med confignotification exit. The appropriate VLANs must exist.
Allow controller to honor VLAN assignments from AAA (sometimes called AAA override). Put your open SSID (if any) in MAC-Authentication mode and authenticate against the FreeRADIUS hosted on PacketFence.
Put your secure SSID (if any) in 802.1X mode and authenticate against FreeRADIUS hosted on PacketFence. On registration / isolation VLANs the DHCP traffic must reach the PacketFence server. On your production VLANs a copy of the DHCP traffic must reach PacketFence where a pfdhcplistener listens (configurable in pf.conf under interfaces). PacketFence Management VLAN: 1 IP address: 192.168.1.5. registration VLAN ID 2, subnet 192.168.2.0/24. isolation VLAN ID 3, subnet 192.168.3.0/24. production VLAN ID 10, subnet 172.16.1.0/24.
the VLANs are spanned in the switches and switching L2 equipments, from the Production Network to the PacketFence server(s). the VLANs are allowed in the trunks.
Aerohive Access Point is loaded with HiveOS with version 6 or later. HiveManager with version 6 or later. Wireless AP: 172.16.1.1. RADIUS Secret: useStrongerSecret. You will need to create one User Profile for each VLANs used, for us, we will create 3 Users Profiles, Registration, Isolation and Production.
from name, give the name of a rule to manage the VLANs with PacketFence (Registration; Isolation; Production). from Attribute Name, give the VLAN ID of the VLAN. from Default VLan, Click on the ( +) (New).
as a VLAN ID, give the VLAN ID earlier Registration(2), Isolation(3) or Production(10). click on Save and click on Save again on the Configure interfaces and User Access. Note Aerohive have a session replication feature to ease the EAP session roaming between two access points.
However, this may cause problems when you bounce the wireless card of a client, it will not do a new RADIUS request. Two settings can be tweaked to reduce the caching impact, it is the roaming cache update interval and roaming cache ageout. They are located in Configuration → SSIDs → SSID Name → Optional Settings → Advanced. The other way to support Roaming is to enable SNMP trap in the Aerohive configuration to PacketFence server. PacketFence will recognize the ahConnectionChangeEvent and will change the location of the node in his base. First because there is no way to detect in the RADIUS request that the request is for an SSID configured for IPSK, you need to configure PacketFence to trigger IPSK on a connection profile. To do that, create a new connection profile, set a Filter based on the SSID (Example SSID PSKSSID), enable IPSK and set a default PSK key.
So each time a device will connect on this specific SSID PacketFence will know that it has to answer with specific VSA attributes. Second step is to associate the device to a user, you have two ways to do it, the first one is to manually edit an user and in Miscellaneous tab fill the PSK entry (8 characters minimum) then edit a node and change the owner with the one you just edit before. The second way to associate the device is to use a provisioner. There are also 2 ways to do it, use the 'IPSK' provisioner (it will show you a page on the portal with the PSK key to use and the SSID to connect to, or use the 'Windows/Apple Devices/Android' provisioner and configure it to do IPSK. FGT50E # config user radius FGT50E (radius) # edit packetfence new entry 'packetfence' added FGT50E (packetfence) # set server 192.168.1.5 FGT50E (packetfence) # set secret useStrongerSecret FGT50E (packetfence) # set nas-ip 192.168.1.1 FGT50E (packetfence) # set radius-coa enable FGT50E (packetfence) # config accounting-server FGT50E (accounting-server) # edit 1 new entry '1' added FGT50E (1) # set status enable FGT50E (1) # set server 192.168.1.5 FGT50E (1) # set secret useStrongerSecret FGT50E (1) # end FGT50E (packetfence) # end.
FGT50E #config wireless-controller vap FGT50E (vap) # edit PF-Secure new entry 'PF-Secure' added FGT50E (PF-Secure) # edit 'PF-Secure' FGT50E (PF-Secure) # set vdom 'root' FGT50E (PF-Secure) # set ssid 'PF-Secure' FGT50E (PF-Secure) # set security wpa2-only-enterprise FGT50E (PF-Secure) # set auth radius FGT50E (PF-Secure) # set radius-server 'packetfence' FGT50E (PF-Secure) # set schedule 'always' FGT50E (PF-Secure) # set local-bridging enable FGT50E (PF-Secure) # set dynamic-vlan enable FGT50E (PF-Secure) # end. $(if chap-id) JavaScript required. Enable JavaScript to continue. $(endif) If you are not redirected in a few seconds, click 'continue' below
Edit the device configuration, and go to Interface → Ethernet Ports. Ensure that the up1 interface is set as trunk, with all the allowed VLANs. Next, create the VLAN under Interface → Virtual Interfaces.
Roles (Per-User Firewall). Since PacketFence 3.3.0, we now support roles for the Motorola hardware using WiNGS 5.x. To add roles, go in Configuration → Security → Wireless Client Roles. First create a global policy that will contain your roles. Next, create your Roles by clicking on the Add button on the bottom right. It is important to configure the Group Configuration line properly by setting the string name that we will use in the RADIUS packet.
For example, for a Guests Role, you can put Group Configuration Exact Guests, and for a Staff Roles, you can put Group Configuration Exact Staff. In the roles configuration in switches.conf, you would have something like. wsTransport is the protocol used to connect to port 8443 of the Unifi controller and should be HTTPS. This is configured in the Web Services tab of the switch. wsUser is a valid administrator username on your Unifi controller.
This is configured in the Web Services tab of the switch. wsPwd is the password that is associated to the wsUser. This is configured in the Web Services tab of the switch.
controllerIp is the IP address of your Unifi controller. This is configured in the Definition tab of the switch.
Manage Wireless Networks Mac
BZ.v3.9.3# cat /tmp/system.cfg grep ssid aaa.1.ssid=PacketFence-Secure wireless.1.ssid=PacketFence-Secure wireless.1.hidessid=false aaa.2.ssid=PacketFence-Public wireless.2.ssid=PacketFence-Public wireless.2.hidessid=false aaa.3.ssid=vport-802AA8863D5B wireless.3.ssid=vport-802AA8863D5B wireless.3.hidessid=true aaa.4.ssid=PacketFence-Secure wireless.4.ssid=PacketFence-Secure wireless.4.hidessid=false aaa.5.ssid=PacketFence-Public wireless.5.ssid=PacketFence-Public wireless.5.hidessid=false.